Analyzing APT Mustang Panda's Latest DLL Sideloading Tactics & Malware Campaign
19 Jun 2025 (2117 Words, 12 Minutes)
Brief Introduction
Mustang Panda (the adversary), a prolific China-aligned cyber espionage group, remains a significant threat in 2025, actively pursuing intelligence gathering operations against governmental, military, and non-governmental organizations. Recent campaigns show a continued focus on targets across Europe and East Asia, with a particular emphasis on entities in Myanmar. The group’s operations are consistently characterized by their signature technique of DLL sideloading, leveraging lures themed as official documents to trick victims into initiating a multi-stage infection process via spear-phishing.
Demonstrating a clear commitment to evading modern defenses, Mustang Panda has recently upgraded its toolkit to enhance stealth and bypass endpoint security. This includes deploying updated variants of their primary TONESHELL backdoor and introducing new specialized tools for lateral movement and keylogging. Most notably, the development of the SplatCloak driver, designed specifically to disable EDR products, underscores their adaptive nature and solidifies their status as a sophisticated and evolving threat actor in the global cybersecurity landscape.
Assets and Indicators of Compromise
Let’s begin our Investigation with couple of IOCs related to Mustang Panda’s latest malware campaign against government & security agencies in Southeast Asia with the Lightpipe payload.
Indicators of Compromise (IOCs)
| Assets | Hash/IP/Files | Link |
|---|---|---|
| (The_Military_Balance_2025).zip | 6d8889f113cdfa27bc76a59c788d6a17 |
VT Link |
| AS 9381 (HKBN Enterprise Solutions HK Limited) | 218.255.96.245 |
VT Link |
☣️[!WARNING!]☣️ Live Assets
Domains and download links shared below are still alive, up and running at the time of writing this blog. In case, one can download them directly, I have defanged the URL for your own safety. Please exercise caution while interacting and handling the malware kits.
- hxxps[://]www[.]mgood[.]co[.]kr/upload/ebook/04-17-2025/Strategic_Minerals_Development_Policy[.]zip
- hxxps[://]www[.]mgood[.]co[.]kr/upload/ebook/04-17-2025/NSC_Meeting_Minutes_Apr2025[.]zip

The adversary has also utilized Google Drive on several occassions to host the malware, my hypothesis for the domain www[.]mgood[.]co[.]kr is that either they exploited unrestricted file upload, or they simply registered on the website and hosted malware over there.
Usually the adversary performs spear phishing against their targets and historically, they have used USB based droppers too.
Starting with (The_Military_Balance_2025).zip :
Initially when unarchived, you’ll see a legitimate chrome binary - although renamed, and to naked eyes you won’t see anything else. We might think where is the malicious DLL which will be sideloaded? Here the adversary has sneakily hidden the folder where the malicious DLL resides.

So, darhs means the directory has all these attributes set: it is a directory (d), marked as archive (a), read-only (r), hidden (h), and system (s).

When a directory or file has both Hidden and System attributes set (like in this case, directory with h and s), it is treated as a protected operating system file. By default, even if you enable “Show hidden files,” Windows Explorer will still hide items marked as system files unless you explicitly disable the “Hide protected operating system files” option in Folder Options.
We can use tools like DLLHound to identify missing DLLs in any running process on the windows machine for the purpose of sideloading. Similarly in this case, we can identify that the module chrome_elf.dll is missing, as legitimate chrome.exe binary looks for it through a particular DLL search order.

DLLHound’s output

Missing DLLs which were not found for legitimate chrome.exe. The malicious chrome_elf.dll is PE32 bit DLL written in C++ which we will analyze in a quick and dirty fashion to infer its behavior.
Digital Signature

Analyzing its digital signature reveals that its likely spoofed or self-signed for evasion. But the certificate chain is terminated at the root CA because it isn’t in the trusted store, hence it gives the user an option to install the cert itself.
In contrary, we can locate legitimate and signed binary (chrome_elf.dll) on the host via this powershell command:
Get-ChildItem -Path C:\ -Recurse -Filter "chrome_elf.dll" -ErrorAction SilentlyContinue
which gets couple of hits with the absolute path being -
1. C:\eSupport\eDriver\Software\Driver\DCH\Online\Graphic\NVIDIA\Graphic_DCH\30.0.14.7186\24344\WIN32UX\GFExperience
2. C:\Program Files\NVIDIA Corporation\NVIDIA GeForce Experience
3. C:\Program Files\Google\Chrome\Application\137.0.7151.105
4. C:\Program Files\Google\Chrome\Application\137.0.7151.120
5. C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF
6. C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1
It seems like chrome_elf.dll file is signed by Adobe, NVIDIA and Google likewise. Depending upon the software and drivers installed on your machine, it might vary.
For reference, here’s the digital signature of signed chrome_elf.dll

Exports

and here’s a comparison between the exports from the malicious chrome_elf.dll and a legitimate one.

When we analyze the function calls from the legitimate chrome.exe binary, we notice these 4 functions being utilized from chrome_elf.dll binary, that’s where the entrypoint of malicious DLL lies.
GetInstallDetailsPayload
IsBrowserProcess
SignalChromeElf
SignalInitializeCrashReporting
CAPA Analysis

Quick CAPA analysis reveals the capabilities of this malicious DLL. We will explore the essential ones manually as well as via sandbox to unearth the details.
Sandbox Analysis - Network Traffic

Quick sandbox execution reveals the trace of TONESHELL.

We can confirm it via analyzing the network packet bytes 17 03 03 which is usually prepended before transacting the encrypted data.
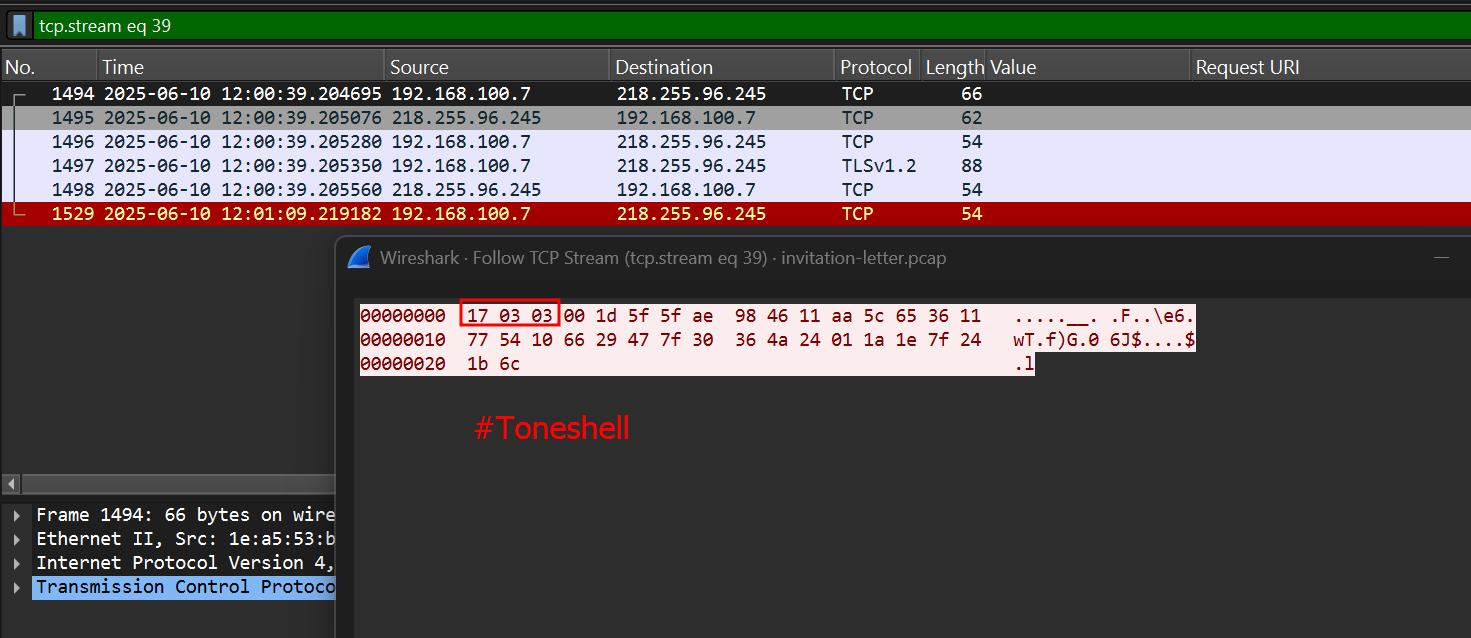
In another variant and campaign of this adversary, we can find the same packet bytes against the suspicious IP address 218.255.96.245. Surprisingly no security vendor has flagged the IP as malicious (as of 10th June 2025).

Multiple network based detection rules (from suricata) are triggered against the binary.

Suspicious IP address it establishes connections with over port 443, surprisingly I didn’t find any domain FQDN resolution against the binary in run-time, besides some legitimate benign network traffic.
Sandbox Analysis - Execution

Once the user/target unarchives and executes the legitimate chrome.exe binary (The_Military_Balance_2025).exe, it immediately sideloads the malicious chrome_elf.dll, which then renames and copies itself to a new location (C:\ProgramData\ChromePDFBrowser\ChromePDF.exe) and (C:\ProgramData\ChromePDFBrowser\101.0.4951.41\chrome_elf.dll). All of this happens via schtasks.exe which ensures task scheduler based persistence. We will delve deeper into its function calls.

Mutex check - CATM20252003 (more on it later).
Besides these details, automated sandbox analyses reveals task scheduler based execution and autorun registry modification for persistence.
Malware Analysis - Execution

Copies itself to C:\ProgramData\ChromePDFBrowser

Stepping through the function calls and analyzing the subroutines, we stumble upon task scheduler based persistence mechanism.
schtasks /F /Create /TN "ChromeBrowser-chromiumim" /SC minute /MO 5 /TR "C:\ProgramData\ChromePDFBrowser\ChromePDF.exe FreePDF"
The primary function of this command is to ensure that the ChromePDF.exe program is executed automatically every five minutes, indefinitely. This high frequency and the use of the /F flag to prevent failure on re-creation are strong indicators of a task designed for persistence.

- which happens simultaneously when sideloading happens, along with popping a MessageBox with the title - Error: File Corrupted & message - The PDF File is corrupted. Please restart your computer to try again.

APT shenanigans, reveals that they’re not a h@x0r and they love America, also previously revealing the GPS co-ordinates (27°40’54.0”N 112°10’26.8”W) of a particular UNESCO world heritage site?!

Moving forward, we confirm the Mutex check - ensuring only one instance of task scheduler entry is running simultaneously.

Malware Analysis - Persistence

When task scheduler runs the binary (C:\ProgramData\ChromePDFBrowser\ChromePDF.exe) it executes its second persistence mechanism - registry run keys.

Name - ChromePDFBrowser
key - HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
value - C:\ProgramData\ChromePDFBrowser\ChromePDF.exe FreePDF
It executes in the context of the user who logs in. MITRE - Autostart Execution - T1547.001

Once the Mutex synchronization check and subsequent function calls has been executed, the malware immediately runs the command shutdown /s /f /t 0, which in immediate effect shuts down the computer, killing any other program.

Shellcode Execution

Upon close inspection, the malicious DLL utilizes EnumFontsW windows callback function pointer to map the shellcode in memory and executed it.
I encountered couple of anti-debugging and anti-sandbox WinAPI calls (IsDebuggerPresent, GetTickCount, etc).
I will delve deeper into shellcode execution and encryption/decryption routines in another blog, but here’s a glimpse of it – surprisingly they’re still using HeapAlloc to allocate memory dynamically, as compared to modern memory management techniques.

Revisiting the exports

GetSPApp(void) –> Mutex check and PDF error route, shutdown and for synchronization purpose. AAfsSetMainStart –> iloveamerica & “Error PDF” messageBox Chrome_start_ipc –> shutdown resolution and mutex checks
This is just a rough description of function calls.
Besides that, we can visualize the Infection Chain as shown below -

Steps of Infection chain would look something like this -

- Adversary sends the phishing email
- User/target downloads the archive, extracts the contents and executes the binary
- Binary sideloads the malicious DLL (chrome_elf.dll)
- Malicious DLL copies itself along with the legitimate binary in a new directory (C:\ProgramData\ChromePDFBrowser or C:\ProgramData\NVIDIAFrameViewSDK etc…)
- And executes itself via task scheduler, which again sideloads the DLL
- User sees the messagebox error prompt - PDF is corrupted…
- In background the registry run key persistence is established.
- Machine shuts down/reboots.
More Malware Samples

Pivoting further through the suspicious IP address, we find more malware samples which are actively used by APT Mustang Panda.

| Malware sample attributes |
|---|
| Legitimate Binary - Invitation for the Paki Ind and 14th PK-IN JWGTI.exe |
| Malicious DLL - libcef.dll 60033579563b1af5fa06e3cd3d6e0951 |
| File Description - Adobe Licensing WF Helper |
| Original Filename - adobe_licensing_wt_helper.exe |
| Signed - ❌ |
| Malware sample attributes |
|---|
| Legitimate Binary - Invitation to the Inter-Agency Meeting for the 46th ASEAN Summit.exe |
| Malicious DLL - helper_core.dll 47dff78a81c694066489b7fdac353f28 |
| File Description - Wargaming.net Game Center |
| Original Filename - helper_process.exe |
| Signed - ❌ |
| Malware sample attributes |
|---|
| Legitimate Binary - Invitation letter for the com Workshop - AMB.exe |
| Malicious DLL - helper_core.dll bd806ab870f06cec107c5ae44442b5fb |
| File Description - Wargaming.net Game Center |
| Original Filename - helper_process.exe |
| Signed - ❌ |
| Malware sample attributes |
|---|
| Legitimate Binary - Bilingual Education Reform Report (སྐད་གཉིས་སློབ་གསོ་བསྒྱུར་བཅོས་སྙན་ཞུ) |
| Malicious DLL - libjyy.dll 5d88adf862e6944b995ac6dd5151588d |
| File Description - FFWallpaper Widgets Jyy |
| Original Filename - libjyy.exe |
| Signed - ✅ Digitally signed by Hefei Nora Network Technology Co., Ltd. |
| Malware sample attributes |
|---|
| Legitimate Binary - DRC Mining, Strategic Minerals Development Policy.exe |
| Malicious DLL - helper_core.dll 2123eab51aa468d5140c3bfe2bbe7775 |
| File Description - Wargaming.net Game Center |
| Original Filename - helper_process.exe |
| Signed - ❌ |
| Malware sample attributes |
|---|
| Legitimate Binary - NSC_Meeting_Minutes_Apr2025.exe |
| Malicious DLL - helper_core.dll 42b3081297597814f82aff32e9d7076d |
| File Description - Wargaming.net Game Center |
| Original Filename - helper_process.exe |
| Signed - ❌ |
More or less the attributes are same, in some sample you won’t find task scheduler based execution and persistence, solely relying on registry run key persistence. With one execption which has the digitally signed malicious DLL. Method of infection and payload containerization has some variations.
- ‘DRC Mining, Strategic Minerals Development Policy.url’ file being the Internet shortcut - hxxps[://]www[.]mgood[.]co[.]kr/upload/ebook/04-17-2025/NSC_Meeting_Minutes_Apr2025[.]zip
- NSC_Meeting_Minutes_Apr2025.lnk - “C:\Windows\System32\conhost.exe –headless –width 80 –height 90 explorer (NSC_Meeting)-0416\NSC_Meeting_Minutes_Apr2025.exe”
From the end user’s perspective, if they will attempt to delete the malicious DLL they will encounter warning message like this -

which is fantastic for invoking doubts in the mind of user.
One can pick up debugging the export function AAfsSetMainStart() to start their malware analysis, mostly it’ll start with greetings from the Mustang Panda. They utilize same good old’ DLL Sideloading tactics against their target, with persistence and little bit of evasion, rest of the job is done by their LightPipe and ToneShell payloads. Today I’ll wrap up the case here.
If you have any questions or need personal guidance then feel free to contact me here
Thanks for spending your time and giving it a read.